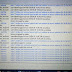
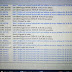
Scriptnya:
/ip firewall filter
add action=add-src-to-address-list address-list=DDOS address-list-timeout=15s \ chain=input comment="" disabled=no dst-port=1337 protocol=tcp
add action=add-src-to-address-list address-list=DDOS address-list-timeout=15m \ chain=input comment="" disabled=no dst-port=7331 protocol=tcp src-address-list=knock
add action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w \ chain=input comment="Port scanners to list " disabled=no protocol=tcp psd=21,3s,3,1
add action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w \ chain=input comment="SYN/FIN scan" disabled=no protocol=tcp tcp-flags=fin,syn
add action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w \ chain=input comment="SYN/RST scan" disabled=no protocol=tcp tcp-flags=syn,rst
add action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w \ chain=input disabled=no tcp-flags=fin,psh,urg,!syn,!rst,!ack protocol=tcp \ comment="FIN/PSH/URG scan"
add action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w \ chain=input disabled=no protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg \
comment="ALL/ALL scan"
add action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w \ chain=input tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg comment="NMAP NULL scan" \ disabled=no protocol=tcp
add action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w \ chain=input comment="NMAP FIN Stealth scan" disabled=no protocol=tcp
add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=0-65535 \ protocol=tcp src-address=61.213.183.1-61.213.183.254
add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=0-65535 \ protocol=tcp src-address=67.195.134.1-67.195.134.254
add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=0-65535 \ protocol=tcp src-address=68.142.233.1-68.142.233.254
add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=0-65535 \ protocol=tcp src-address=68.180.217.1-68.180.217.254
add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=0-65535 \ protocol=tcp src-address=203.84.204.1-203.84.204.254
add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=0-65535 \ protocol=tcp src-address=69.63.176.1-69.63.176.254
add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=0-65535 \ protocol=tcp src-address=69.63.181.1-69.63.181.254
add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=0-65535 \ protocol=tcp src-address=63.245.209.1-63.245.209.254
add action=accept chain=input comment="ANTI NETCUT" disabled=no dst-port=0-65535 \ protocol=tcp src-address=63.245.213.1-63.245.213.254